Your Network Security Requires Your Attention.
It's BAD out there!.
Contact Us To Know MoreBest prices in the market

EXPLOIT
A malicious application or script that can be used to take advantage of a computer’s vulnerability.
VECTOR
An attack vector is a pathway or method used by a hacker to illegally access a network or computer in an attempt to exploit system vulnerabilities.
BREACH
The moment a hacker successfully exploits a vulnerability in a computer or device, and gains access to its files and network.
ACTOR
a threat actor is an entity responsible for a cybersecurity incident. They are referred to as “actors” because it is a neutral term that avoids labeling them as an individual, group, or collection of multiple groups.
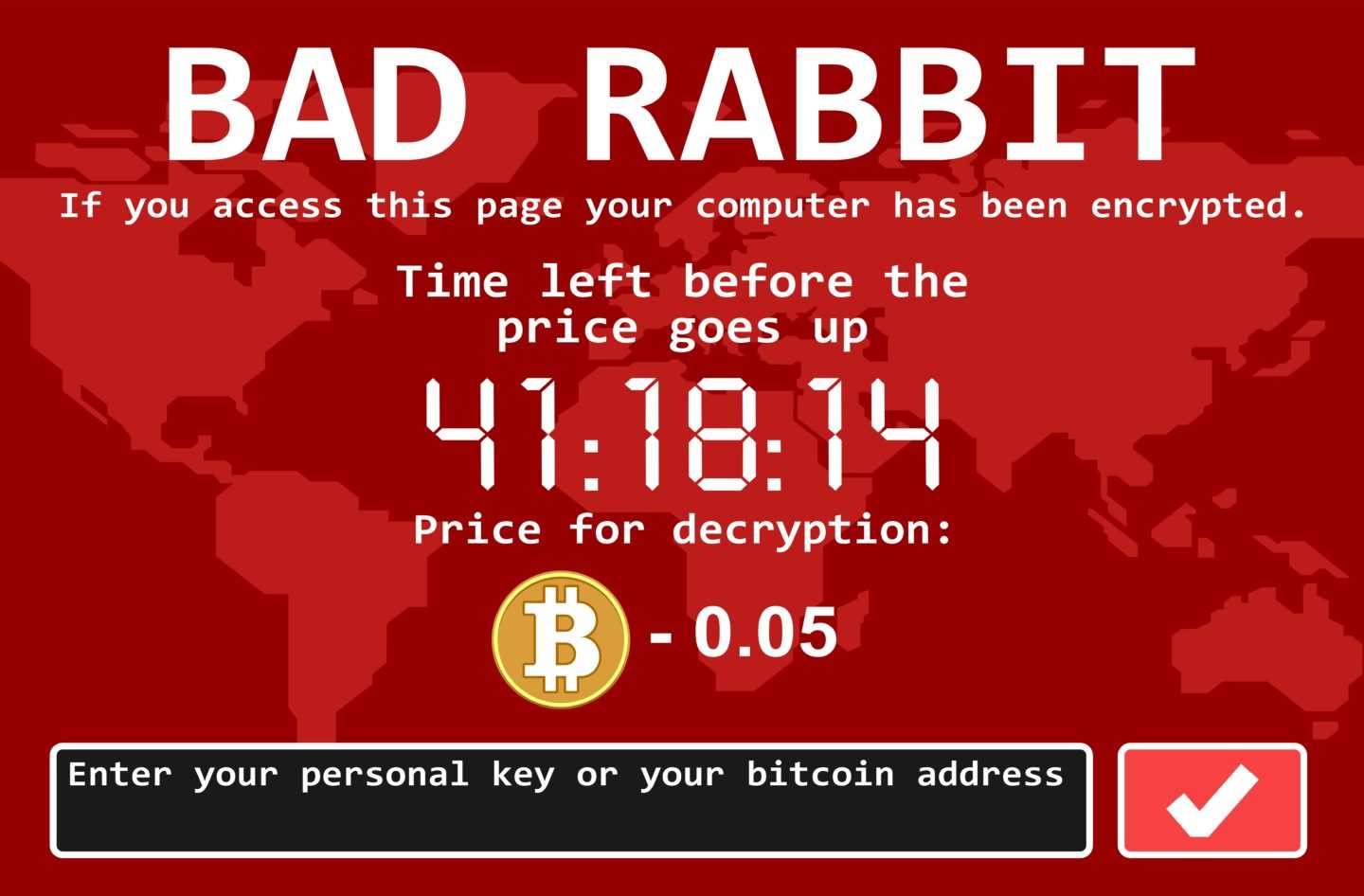
RANSOMWARE
A form of malware that deliberately prevents you from accessing files on your computer – holding your data hostage.
PHISHING
A technique used by hackers to obtain sensitive information. For example, using hand-crafted email messages designed to trick people into divulging personal or confidential data such as passwords and bank account information.

Keep Your Business Safe On The Internet
Strong passwords, backups, user training and software updates are a few of a group of measures you need in place to keep the system away from hackers.
Contact us To Learn More